In today’s digital age, security is not just a “nice-to-have” — it’s a business imperative. To remain viable, competitive and even operational, businesses must prioritize their security infrastructure.
We understand the relentless security challenges you face daily. With Secur-Serv as your trusted managed security services provider (MSSP), we’ll help you reinforce your defenses, reduce vulnerabilities and adopt a truly proactive security stance.
Let your team focus on core business projects, confident that your cybersecurity and network safety are in expert hands with a trusted MSSP.
Secur-Serv’s Managed Security Services
Security solutions tailored to today’s dynamic business landscape.
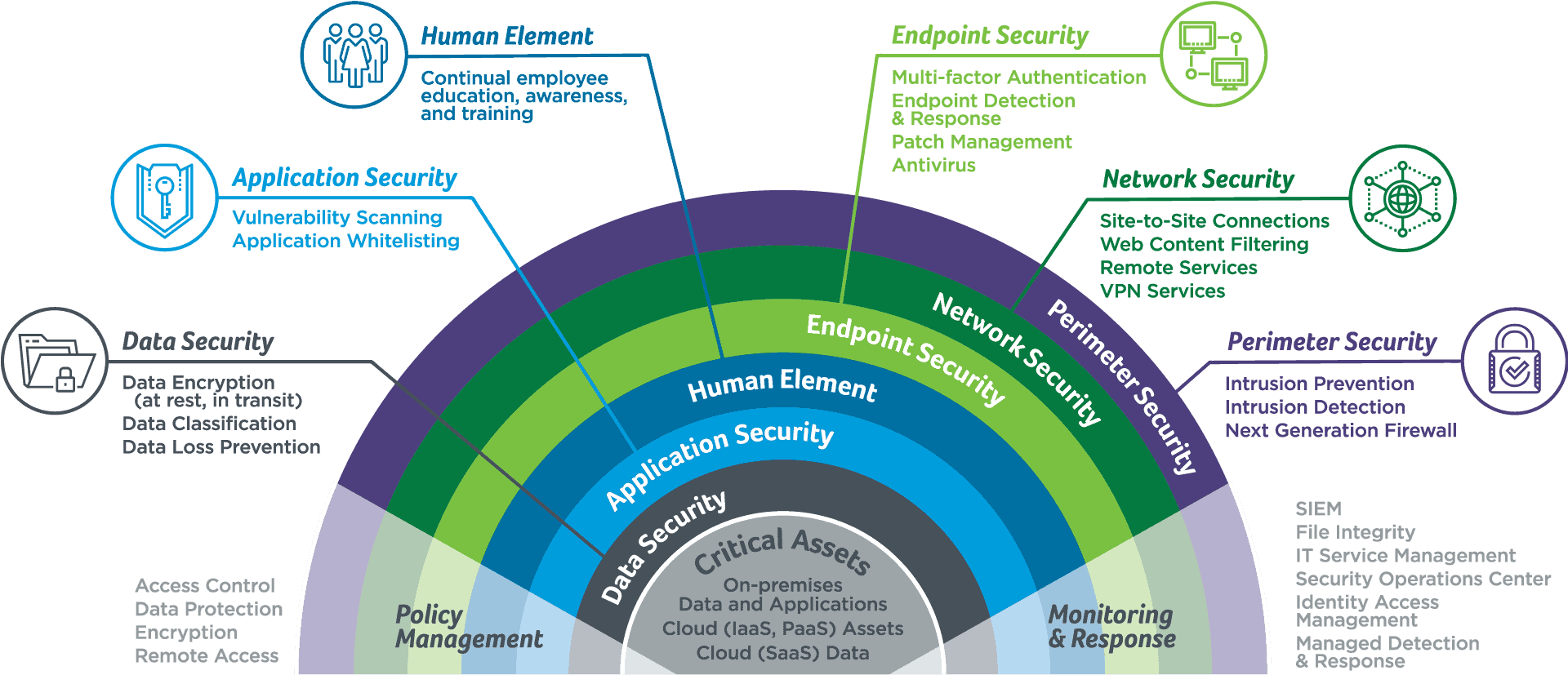
Multi-Layer Security Approach
Multiple security protection options for your business
The Human Layer
Employees are our first line of defense when warding off attacks. Continually educate and train your entire staff with the help of Secur-Serv.
Perimeter Security
Behavior monitoring detects and alerts you to any suspicious activity using Intrusion Prevention Services (IPS), Intrusion Detection Services (IDS), and Next-Generation Firewall Services.
Network Security
Rules and configurations to secure accessibility and integrity. Secur-Serv offers Site-to-Site Connections, Web Content Filtering, Remote Services, and VPN Services.
Application Security
Every time you deploy new application features or update existing ones, your security measures need to adapt. Vulnerability Scanning and Application Whitelisting (Safelisting) help secure your applications
Data Security
Data encryption (at rest, in transit), data classification, and data loss prevention are three services Secur-Serv offers to help keep your most valuable asset safe – your data
Policy Management
Manage the rules and procedures everyone must follow when accessing and using your IT assets and resources with Access Control, Data Protection, Encryption, and Remote Access
Monitoring and Response
It is critical to monitor, detect, contain and remediate attacks. Through tools like SIEM, File Integrity, IT Service Management, Security Operation Center (SOC), Identity Access Management and Managed Detection and Response Secur-Serv has the security solutions you need for better security protection.
Total Defense: Managed Cybersecurity Packages
With 43% of cyberattacks targeting small businesses, the threat is real. Take cybersecurity seriously. Our packages offer simple, affordable solutions to fortify defenses and protect what matters most.
Visible Tools for Invisible Attacks
Blindspots in security are no longer acceptable. A single-point security solution is insufficient in today’s complex digital landscape. Backed by security and operational experts, a holistic defense-in-depth approach enables you to reduce risks and shield your data from lurking threats.
Secur-Serv offers multiple security options to help build the most comprehensive security solution for your business. In addition to security services, our experts also assist in compliance and audit reviews to help you reach even the most stringent standards. See how we can help you modernize your security infrastructure to keep your business running efficiently and affordably.
Watch our on-demand webinar to learn more about how your company can benefit from cybersecurity and cyber resilience efforts.
Annual Security Assessment
No more wondering, “Is my business protected?”. Secur-Serv assesses your environment to make sure you have the proper security layers aligned with your business. You can stop overpaying for unused services or implementing the wrong services, which could leave you and your data exposed to threats.
Security Audit and Cyber Insurance Assistance
Secur-Serv conducts regular audits to make sure your security services are evolving as your business grows. Plus, our security experts can help you navigate complex cybersecurity insurance questionnaires and requirement validations.
We also offer audit assistance for companies who must adhere to high compliance standards such as HIPAA, FISMA, FFIEC, PCI-DSS, FERPA, GLBA and others.
Frequently Asked Questions
What are managed security services?
Managed security services involve a suite of solutions designed to protect businesses from cybersecurity threats. They typically include monitoring, threat detection and incident response, among others. Keep in mind that managed security services do not just encompass tool deployment but the management, consultation and expertise you receive as well.
What is a managed security services provider (MSSP)?
An MSSP is a company that offers specialized services related to information security, monitoring and management, often delivered remotely. They provide expertise, technology support and continuous oversight to help businesses protect their data, detect threats and respond to security incidents.
How does Secur-Serv differ from a typical managed security provider?
While Secur-Serv offers solutions comparable to leading MSSP services, our focus is on a tailored approach, ensuring businesses receive security measures that align closely with their specific needs and goals. Furthermore, Secur-Serv offers affordable solutions specifically for small- to medium-sized businesses (SMBs). And we take security seriously — so much that we require a baseline security package for our managed IT customers.
What makes Secur-Serv’s managed security services stand out?
Secur-Serv emphasizes a bespoke security strategy, ensuring services are fine-tuned to the unique challenges your business faces. Our approach offers the robust protection synonymous with leading MSSPs but with a personalized touch.
Why should I consider managed security services for my business?
It’s not a question of if your business will face a cyberattack but a question of when. It’s no longer an option to go without security services. It’s all about prevention, detection, mitigation and recovery. Managed security services ensure your business is equipped to counter evolving threats. With Secur-Serv, you get proactive defense mechanisms, similar to the offerings of leading MSSPs, ensuring your data and infrastructure remain protected.
What industries does Secur-Serv specialize in protecting?
Secur-Serv specializes in protecting a variety of sectors, including Manufacturers, Financial Institutions including community banks and credit Unions, and the Transportation and Logistics industry. Our tailored solutions address the unique vulnerabilities of each industry, ensuring robust, industry-specific protection.
How does Secur-Serv ensure its security measures remain up-to-date?
Secur-Serv employs a dedicated team of experts who constantly monitor the cybersecurity landscape. We regularly update and adapt our solutions to counter the latest threats and ensure optimal protection for our clients. Additionally, we partner with leading cybersecurity businesses, employ certified security experts and are part of various security industry groups.